View Menu – User Security
Purpose: To use when Level Security is not set.
Please read Set Passwords to Control Security before continuing.
Preparation:
– Appoint and publish the name of the System Administrator.
– Draft, agree and publish the Security Policy – consider issuing copies for staff to sign as appropriate.
– Decide on which type of system security to use.
– Assign access rights and agree these with Department Managers.
– Ensure any changes in Access Rights are properly authorised in accordance with Security Policy requirements.
Processing :
On the main menu click View > Security > User Security to open form.
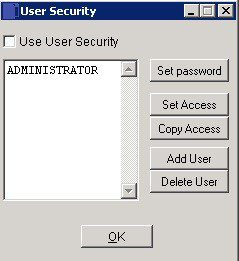
Check box ‘Use User security’
Processing now follows a series of logical steps, namely;
– Adding Users.
– Setting Passwords.
– Creating Access Rights – existing user rights can be copied to new users.
– Deleting users as required.
Add User: Click buttom and complete form:
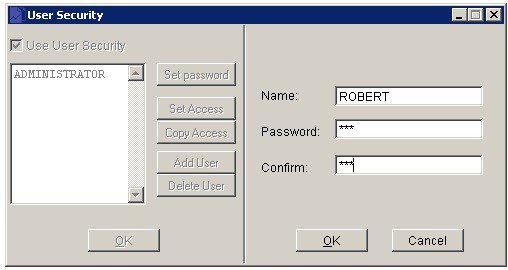
Setting passwords: Use something memorable – the password is case sensitive and in ‘Confirm‘ must be identical. Click on the Set Password button at any time to change the password.
Set Access Rights: Highlight the user’s name and click on ‘Set Access‘ then this box opens –
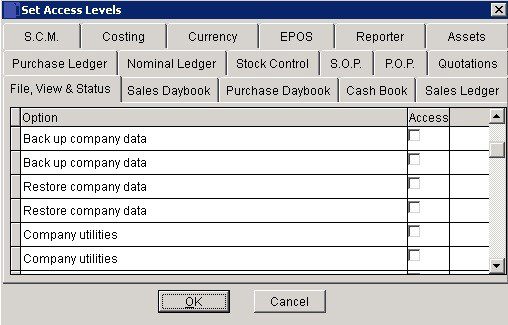
Click relevant tab to select required page.
Select the required task from the list displayed by using the scroll bar at the right of the page.
Check box aligned with a task to allow Access Rights to use that task.
When you have finished, click OK to close the form and update records. You will be reminded that you need to restart the system for changes to take effect.
When you next start your Prelude Desktop product you will be presented with a list of usernames. Click your username and then type your password into the field. The software will start as normal, but you will find that any inaccessible menu options are greyed out and you will be unable to access them.
Copy another User’s Access Rights:
Access Rights are copied from a Source User to a Target User. Administrator Access Rights cannot be copied.
On the main menu click View > Security > User Security to open the form.
Click on the required Username to select the Source User from the list displayed
Click Copy Access button to open form.
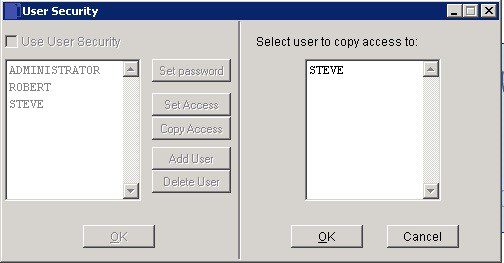
Click on the required Username to select the Target User.
Click the OK button to open a message box. Click Yes to copy access rights.
Click Cancel to close form.
At any time, click Cancel to close the form without update.
Delete a User:
Use this when staff leave the business or when making major changes to a set of Access Rights.
On the main menu click View > Security > User Security to open the Add User form.
Click to highlight the required Username from the list displayed.
Click Delete User button to open a message box. Click Yes to delete user. Selected username is removed from the list.
Ongoing Control:
The System Administrator should keep a log of access rights (in a secure place), noting when these change. Passwords should be changed regularly, in line with the Security Policy recommendations.

0 Comments