View Menu – Login-Based Security (Restrictions)
Purpose: To configure the system for Task-Based Security-Access & Passwords. Please read Set Passwords to Control Security before continuing. Use to add Users and define their options (Restrictions).
Processing:
On the main menu click View > Security > Restrictions to open form.
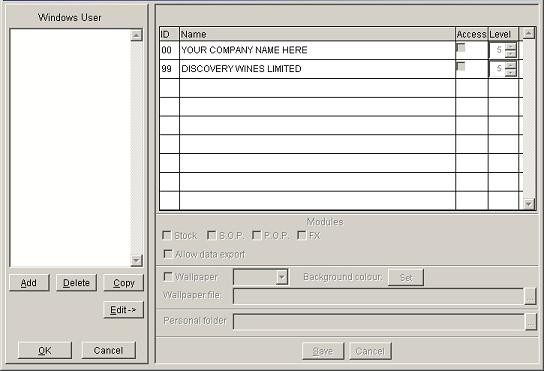
Processing now follows a series of logical steps, namely;
– Adding users.
– Creating Access Rights profiles – an existing profile can be copied to new users.
– Deleting users, as required.
Adding Users:
On the form click Add to open a second form.
On the form enter the new user’s Windows User name. Confirm this with your network administrator.
Click OK to close the form and create the new system user.
At any time, click Cancel to close the form(s) without update.
Creating Access Rights profiles:
Highlight the required user name in the Windows User panel and click Edit. The right part of the form becomes active.
Access: Check the boxes of the companies you wish the user to access. The system will not allow processing of data for unchecked companies.
Level: Click up and down to set the required Task-Based Access to each company for this user.
Modules: Check the boxes of the modules menus you wish the user to access.
Wallpaper: Set user-specific wallpaper and background settings – see General Parameters – Miscellaneous Page.
Personal folder: Set a specific destination folder for all output from the system – Normally U:\Documents\Prelude
When you have finished, click Save then OK to close the form and update records.
At any time, click Cancel to close the form without update.
Copy another User’s Access Rights:
Access Rights profiles are copied from a Source User to a new Target User.
Highlight the Source User in the Windows User panel and click Copy to open a second form.
Type the new Target User name. This must be a new user who does not already feature in the Windows User panel.
Click OK to close the form and create the new system user.
At any time, click Cancel to close the form(s) without update.
Delete a User:
Use this when staff leave the business or when making major changes to a set of Access Rights.
Highlight the user to be deleted in the Windows User panel and click Delete.
Click Yes to delete the user or No to return to the form.
Ongoing Control:
The System Administrator should keep a log of Access Rights (in a secure place), noting when these change. Passwords should be changed regularly, in line with the Security Policy recommendations.

0 Comments